Denis Foo Kune, Ph.D.
I am a scientist, engineer, and founder. I focus on security. I launched the cyber-security startup Virta Laboratories with my two co-founders, Ben Ransford and Kevin Fu. In the past few years, I have been working on clinical systems, medical devices, and side-channel analysis. Prior to that, I was working on cellular networks and internet routing.
I did my postdoc at the University of Michigan with Kevin Fu. I received my Ph.D. from the University of Minnesota while working with Nick Hopper and Yongdae Kim. My thesis focused on improving security on the wireless medium. I looked at electromagnetic interference attacks on time-varying voltage sensors and vulnerabilities on wireless WAN protocols.
In my spare time, I kiteboard.
Security startup
Virta Labs provides security tools tailored to healthcare. With a decade of experience in healthcare security, the team at Virta understand the importance of safety and clinical workflow. Virta Labs help healthcare IT focus on the risks that matter.
Cardiac therapy in the developing world is very limited, while good devices are discarded in the USA.
Chosen electromagnetic waveforms can be used to force signal injection on analog sensors.
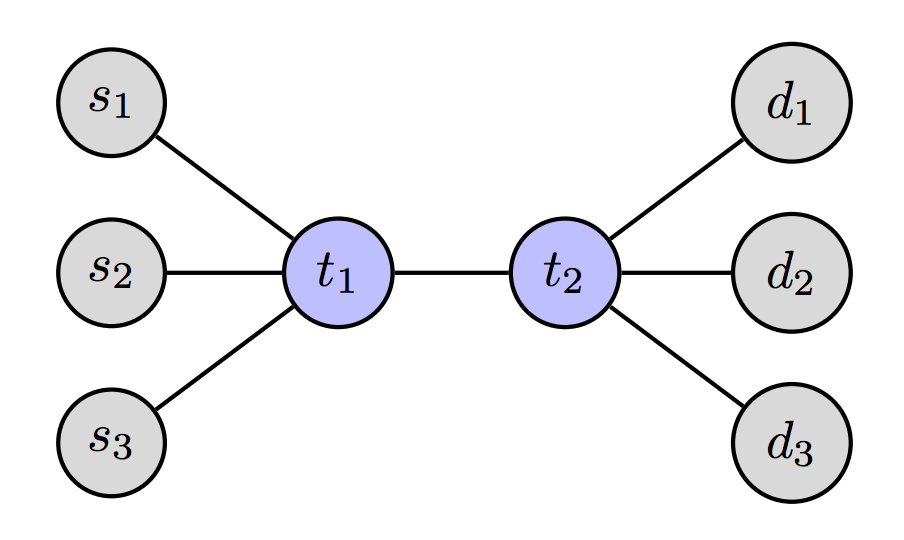
Part of the map of the US FDA 510(k) devices showing the equivalence relationship between devices.
Medical devices and clinical networks
Cybersecurity and medical devices: A Practical guide for cardiac electrophysiologists, Benjamin Ransford, Daniel B Kramer, Denis Foo Kune, Julio Auto de Medeiros, Chen Yan, Wenyuan Xu, Thomas Crawford, Kevin Fu, Pacing and Clinical Electrophysiology, 2017
Cleaning and Sterilization of Used Cardiac Implantable Electronic Devices With Process Validation: The Next Hurdle in Device Recycling, Thomas C Crawford, Craig Allmendinger, Jay Snell, Kevin Weatherwax, Balasundaram Lavan, Timir S Baman, Pat Sovitch, Daniel Alyeshmerni, Thomas Carrigan, Noah Klugman, Denis Kune, Andrew Hughey, Daniel Lautenbach, Nathan Sovitch, Karman Tandon, George Samson, Charles Newman, Sheldon Davis, Archie Brown, Brad Wasserman, Ed Goldman, Sandra L Arlinghaus, Hakan Oral, Kim A Eagle. Journal of the American College of Cardiology (JACC) Clinical Electrophysiology, 2017
Noninvasive Postmarket Security Monitoring for Medical Devices, Benjamin Ransford, Denis Foo Kune, Ann Gookin, Andrew DeOrio, Journal of Medical Devices 2016
SoK: Security and Privacy in Implantable Medical Devices and Body Area Networks, Michael Rushanan, Aviel D Rubin, Denis Foo Kune, Colleen M Swanson, IEEE Securityand Privacy 2014
Ghost Talk: Mitigating EMI Signal Injection Attacks against Analog Sensors, Denis Foo Kune, John Backes, Shane Clark, Dan Kramer, Matthew Reynolds, Kevin Fu, Yongdae Kim, and Wenyuan Xu. In Proceedings of the 34th Annual IEEE Symposium on Security and Privacy 2013
Book chapter: Design Challenges for Secure Implantable Medical Devices, Benjamin Ransford, Shane S Clark, Denis Foo Kune, Kevin Fu, Wayne P Burleson, 2014
Towards a safe integrated clinical environment: a communication security perspective, Denis Foo Kune, Krishna Venkatasubramanian, Eugene Vasserman, Insup Lee, Yongdae Kim, Proceedings of the 2012 ACM workshop on Medical communication systems
Making the invisible visible -- Dependencies in the FDA 510(k) database, Tingyi Wei, Denis Foo Kune, Kevin Fu, HealthTech 2013 - Poster session
Listening on the broadcast paging channel of cellular networks doesn't take much and can reveal the location information of a user.
Cellular Networks
Gaining Control of Cellular Traffic Accounting by Spurious TCP Retransmission, Younghwan Go, EunYoung Jeong, Jongil Won, Yongdae Kim, Denis Foo Kune, KyoungSoo Park, Network and Distributed System Security Symposium (NDSS) 2012
Impact of Malicious TCP Retransmission on Cellular Traffic Accounting, Younghwan Go, Denis Foo Kune, Shinae Woo, KyoungSoo Park, Yongdae Kim, Proceedings of ACM S3 Workshop 2013
Towards Accurate Accounting of Cellular Data for TCP Retransmission, Younghwan Go, Denis Foo Kune, Shinae Woo, KyoungSoo Park, Yongdae Kim, Proceedings of the 14th ACM International Workshop on Mobile Computing Systems and Applications (HotMobile'13)
Location Leaks on the GSM Air Interface, Denis Foo Kune, John Koelndorfer, Nicholas Hopper, Yongdae Kim, 19th Network and Distributed System Security Symposium (NDSS) 2012. Media coverage: Ars Technica, Physorg, Slashdot, MSNBC, TG Daily, IEEE Internet Computing Magazine, Network World, e! Science News, Scientific Computing, gizmag, PC Advisor, Mobile Magazine, The CyberJungle, Inquisitr, MPR, Fox Twin Cities
Efficient private proximity testing with GSM location sketches, Zi Lin, Denis Foo Kune, Nick Hopper, Financial Cryptography and Data Security 2012
Controlling a botnet to focus data traffic on a target BGP router can cause it to drop control-plane traffic.
Time intervals between clicks reveals the distance between keys and narrows the PIN search space.
Other
Secure Encounter-based Mobile Social Networks: Requirements, Designs, and Tradeoffs, Abedelaziz Mohaien, Denis Foo Kune, Eugene Vasserman, Myungsun Kim, Yongdae Kim, IEEE Transactions on Dependable and Secure Computing (IEEE TDSC) 2013
Losing control of the internet: using the data plane to attack the control plane, Max Schuchard, Abedelaziz Mohaisen, Denis Foo Kune, Nicholas Hopper, Yongdae Kim, Eugene Y Vasserman, 18th Network and Distributed System Security Symposium (NDSS) 2011. Media coverage: New Scientist , ZDNet, CBS News, Metro (UK) , The Register (UK)
Timing attacks on PIN input devices, Denis Foo Kune, Yongdae Kim, Proceedings of the 17th ACM conference on Computer and communications security (CCS poster session) 2010
Attacking the Kad Network-Real World Evaluation and High Fidelity Simulation using DVN, E Chan-Tin, P Wang, J Tyra, T Malchow, D Foo Kune, N Hopper, Y Kim, Wiley Security and Communication Networks, 2009
Starburst99: synthesis models for galaxies with active star formation, Claus Leitherer, Daniel Schaerer, Jeffrey D Goldader, Rosa M González Delgado, Carmelle Robert, Denis Foo Kune, Duilia F De Mello, Daniel Devost, Timothy M Heckman, The Astrophysical Journal Supplement Series, Volume 123, 1999